Network Security Audit 101: Keeping Your Business Safe and Sound
A network security audit is a comprehensive evaluation of your organization’s IT infrastructure to identify vulnerabilities, assess security controls, and ensure compliance with regulatory standards. With cyber threats growing more sophisticated each day, protecting your business data has never been more important.
Quick Answer: What is a network security audit?
| Network Security Audit Defined | Key Components |
|---|---|
| A systematic review of network systems, devices, and policies to identify security vulnerabilities and compliance gaps | • Network device inventory • Security policy review • Vulnerability scanning • Penetration testing • Risk assessment • Access control evaluation • Compliance verification |
Every week, businesses face over 1,636 cyberattacks, and the average data breach now costs an all-time high of $4.88 million. These aren’t just numbers—they represent real threats to your retail business’s survival. In fact, data breaches rose 72% from 2021 to 2023, with 22% of organizations experiencing six to ten breaches.
For retail businesses like yours, a network security audit isn’t just an IT checkbox—it’s essential protection for your customer data, payment systems, and business operations. Without regular audits, even minor configuration errors can quickly escalate into significant security risks that threaten everything you’ve built.
“You can’t eliminate all risks. But you’d better be able to foresee a lot of them and do what you can to minimize the impact,” notes Dan Power, a data governance expert. This perfectly captures why network security audits matter—they help you see problems before they become disasters.
Think of a network audit as a regular health checkup for your business technology. Just like skipping doctor visits can lead to undetected health problems, neglecting network security audits leaves vulnerabilities hidden until it’s too late.
What is a Network Security Audit?
A network security audit is much more than just a technical checkup—it’s a comprehensive health assessment for your entire digital ecosystem. Think of it as having a trusted security expert walk through your business, carefully examining every potential entry point, from the obvious front door to that tiny window you forgot existed in the back office.
When we conduct a network security audit at Smart Technologies of Florida, we’re essentially creating a complete picture of your organization’s security landscape. We carefully evaluate all of your network-connected assets—your servers, routers, employee workstations, mobile devices, and even those seemingly innocent IoT gadgets that might be hiding in plain sight.
“Every week, businesses face over 1,636 cyberattacks. This staggering number is a clear reminder that network security is highly essential.” – SentinelOne, November 2024
The beauty of a thorough network security audit isn’t just finding problems—though that’s certainly important. It’s about strengthening your entire security foundation and building resilience against changing threats. Think of it as preventative medicine for your business technology.
Let’s be honest—can you name a single business today that doesn’t rely on computers or internet connectivity? This universal dependence on technology means that virtually every organization, regardless of size or industry, has become a potential target for cybercriminals. The corner coffee shop, the local dentist’s office, the manufacturing plant—they’re all in the crosshairs.
That’s why regular network security audits have become essential business practice. They help you identify and patch vulnerabilities before they can be exploited, potentially saving you from devastating data breaches, operational disruptions, and the legal nightmares that often follow security incidents.
In today’s threat landscape, a network security audit isn’t a luxury or an IT department wish-list item—it’s a fundamental business necessity that protects everything you’ve worked so hard to build.
How to Conduct a Network Security Audit
Ready to strengthen your digital defenses? After 23 years of protecting businesses like yours, we’ve fine-tuned our network security audit process to catch vulnerabilities before hackers do. Let me walk you through our approach—it’s thorough but completely manageable with the right partner.
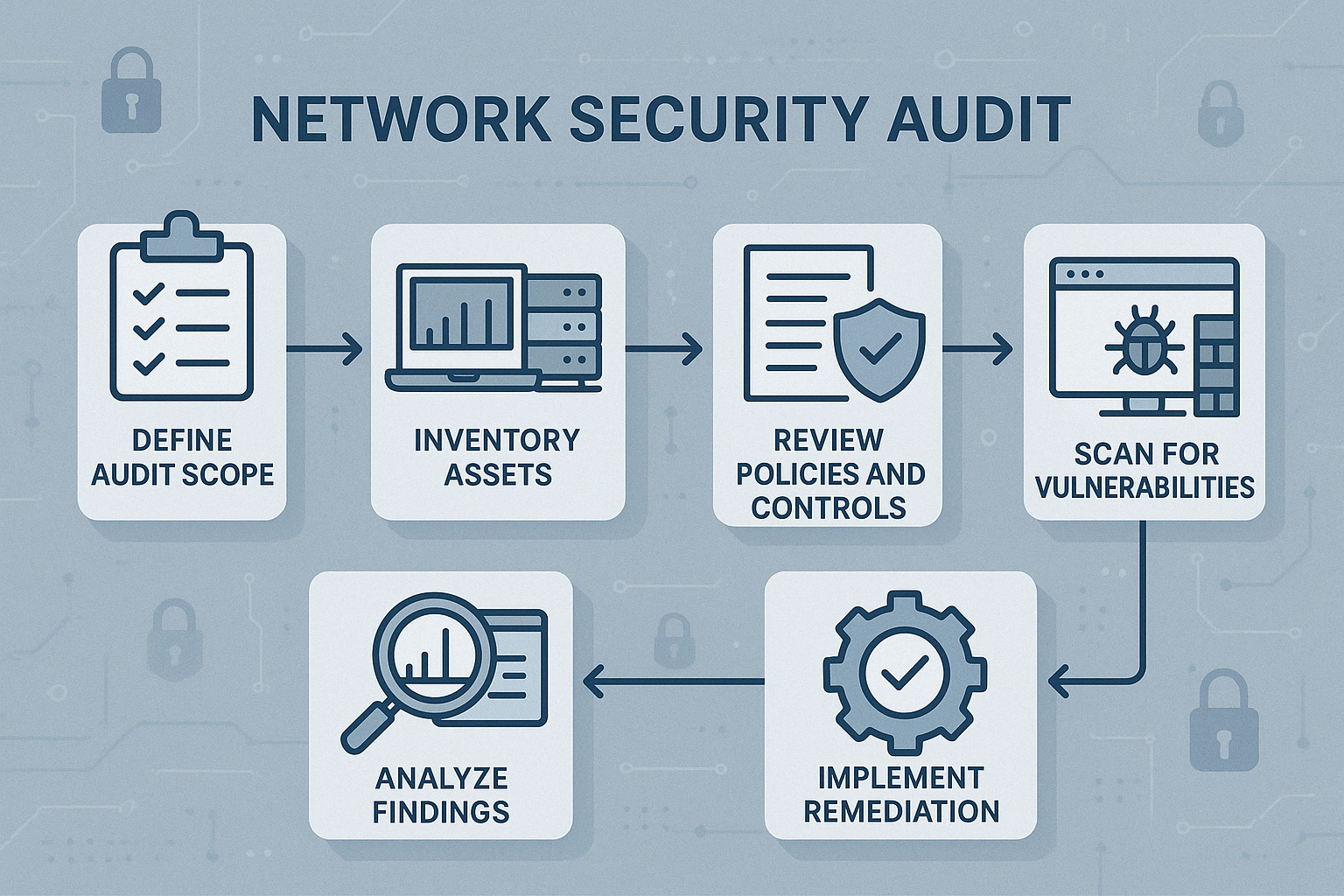
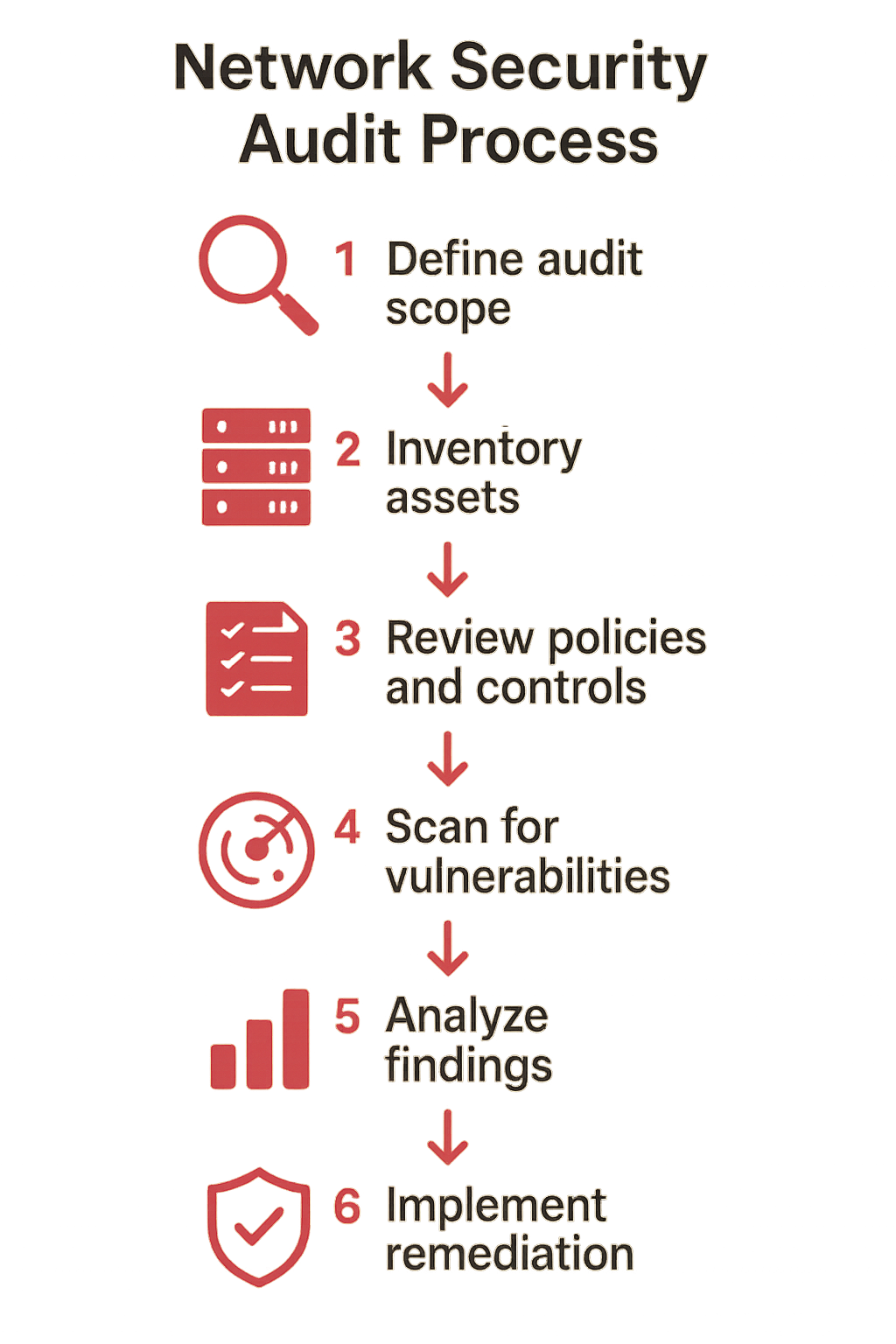
Step 1: Define the Scope of Your Network Security Audit
Before diving into technical details, we need to establish clear boundaries. Think of this as deciding which rooms in your house need the most attention before a deep clean.
What exactly are we looking at? For retailers, this might mean focusing on your point-of-sale systems and customer databases. Healthcare providers naturally prioritize patient records and medical devices. By identifying your most valuable digital assets upfront, we ensure nothing critical falls through the cracks.
We’ll also determine timeframes that work with your business rhythm—because security shouldn’t disrupt your operations. Getting key stakeholders involved early creates buy-in across departments and makes the entire process smoother.
Step 2: Inventory All Network Assets
You can’t protect what you don’t know exists! This crucial step often reveals surprising findings—like that forgotten server in the closet or the department that started using an unapproved cloud service.
A thorough inventory captures everything: your servers, workstations, routers, software applications, cloud resources, data storage locations, and every access point to your network. These “unknown” elements frequently represent your biggest security risks.
Modern networks change constantly, which is why we use specialized tools to create accurate, living inventories that catch even the most elusive components. This foundation makes everything that follows more effective.
Step 3: Assess Security Policies and Compliance
With your digital landscape mapped, we examine how well your security policies protect it—and whether you’re meeting regulatory requirements.
We’ll review how you manage access controls, passwords, data protection, incident response, and employee security training. If you’re like most of our clients, there’s usually room for improvement in how consistently these policies are followed.
For regulated industries, compliance adds another layer to consider. Depending on your business, you might need to align with GDPR, HIPAA, PCI DSS, or other standards. Each framework has specific requirements that must be woven into your security practices. The NIST Cybersecurity Framework offers excellent guidance if you’re looking to establish more robust security practices.
Step 4: Conduct Risk Assessments
Now we transform technical findings into business insights by identifying what threats could actually harm your company. This isn’t about theoretical problems—it’s about real risks to your operations and reputation.
We’ll identify potential threats like malware, phishing attempts, and insider risks, then evaluate how likely they are and what damage they could cause. A financial services company might prioritize customer data breaches, while a manufacturer might focus on threats that could halt production.
We use a visual risk matrix approach that makes these priorities crystal clear, even to team members without technical backgrounds. This common understanding is invaluable when making security decisions.
Step 5: Perform Vulnerability Scanning and Penetration Testing
Here’s where we roll up our sleeves and actively hunt for weaknesses in your systems. First, we use specialized tools to scan for known vulnerabilities—missing patches, outdated software, misconfigurations, weak passwords, and open ports.
Then comes the more hands-on approach: penetration testing. This is essentially ethical hacking where we attempt to exploit those vulnerabilities just like a real attacker would. The insights from this testing are often eye-opening, revealing security gaps that automated scans miss.
We might test from outside your network (like a hacker would), from inside (simulating an employee gone rogue), or focus specifically on your web applications. Sometimes we even include social engineering tests to see if your team might accidentally give away access.
Step 6: Analyze Network Security Audit Findings and Prioritize Risks
With data in hand, we help you make sense of what we’ve found. Not all vulnerabilities deserve equal attention—a critical vulnerability in a low-priority system might be less urgent than a moderate issue in your core business application.
We categorize findings by severity, identify patterns, and connect technical issues to potential business impacts. This risk-based approach ensures you focus resources where they’ll make the biggest difference.
For instance, if we find both outdated software on an internal development server and weak encryption on your customer payment portal, we’d typically recommend addressing the payment portal first. Why? Because it directly impacts customer data protection and regulatory compliance.
Step 7: Remediate and Implement Security Measures
Finding problems is only half the battle—fixing them is where real security happens. We’ll develop a detailed remediation plan that balances security improvements with your operational needs.
Most commonly, this includes applying security patches, reconfiguring systems to follow best practices, implementing additional security controls, strengthening authentication, enhancing network segmentation, and updating security policies.
We understand that security improvements can’t bring your business to a halt, so we carefully plan implementations to minimize disruption. Our goal is to strengthen your security without sacrificing productivity.
Step 8: Document and Report Findings
Clear documentation transforms technical findings into actionable business intelligence. We create comprehensive reports that include an executive summary for leadership, detailed findings with risk assessments, prioritized recommendations, compliance status, and comparison with previous audit results when available.
This documentation serves multiple purposes—it provides a roadmap for security improvements, creates a baseline for future comparisons, supports compliance requirements, and demonstrates your commitment to security. Most importantly, it translates technical jargon into business language everyone can understand.
Step 9: Continuously Monitor and Review
A network security audit isn’t a one-and-done project—it’s part of an ongoing security program. The digital landscape changes constantly, and your security must evolve with it.
We recommend combining periodic formal audits with continuous automated monitoring, regular vulnerability scanning, and prompt assessment whenever you add new systems or make significant changes. Modern tools like Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) systems provide real-time visibility into your security posture.
As we often tell our clients, “The sooner you act, the safer your systems will be.” Continuous monitoring allows you to catch and address new threats before they can cause damage—turning security from a periodic project into a constant protection for your business.
Benefits of Regular Network Security Audits
When you invest in regular network security audits, you’re not just checking boxes—you’re building a stronger, more resilient business. Over our 23 years helping Florida businesses, we’ve seen how these audits transform security from a constant worry into a competitive advantage.
Improved Security Posture
Think of your network security like layers of an onion. Each audit adds another protective layer by identifying and addressing vulnerabilities before hackers can exploit them. Our clients sleep better knowing their defenses grow stronger with each assessment, creating a robust shield around their critical business assets.
Improved Threat Detection
Regular audits help you understand what “normal” looks like in your network. When you know your baseline, unusual activities stand out like a sore thumb. One of our retail clients spotted a potential data breach within minutes because their recent audit had helped them establish clear patterns of typical network behavior.
Reduced Organizational Risk
“By identifying potential security vulnerabilities and addressing them early, the risk of cyberattacks significantly diminishes.”
This isn’t just about preventing technical problems. A single breach can trigger a cascade of financial penalties, legal battles, and reputation damage that many small businesses never recover from. Regular audits help you avoid these devastating scenarios by addressing small issues before they become major crises.
Increased Compliance
For many Daytona Beach businesses, regulatory compliance isn’t optional. Healthcare providers need HIPAA compliance, retailers must follow PCI DSS standards, and many organizations face GDPR requirements. Regular network security audits provide documentation that proves you’re meeting these obligations, helping you avoid hefty fines and legal complications.
Improved Policy Management
Audits often reveal surprising gaps between your security policies on paper and what’s actually happening in your network. One manufacturing client finded their carefully crafted password policy wasn’t being enforced on several critical systems. Finding and fixing these disconnects leads to more effective security across your organization.
“Shadow IT” sounds mysterious, but it’s simply the laptops, smartphones, and cloud services that employees bring into your network without approval. These unauthorized additions create security blind spots that regular audits can reveal and address before they become entry points for attackers.
Facilitating Risk-Based Decision Making
Security budgets aren’t unlimited, so knowing where to invest matters. Audit results give you clear, data-driven insights about your biggest vulnerabilities, helping you prioritize spending where it counts most. This targeted approach delivers better protection without wasteful spending.
Building Cyber Resilience
Perfect security doesn’t exist—but resilience does. Regular audits help you develop the ability to quickly detect, respond to, and recover from security incidents. It’s like the difference between hoping you never get sick versus building a strong immune system that can fight off whatever comes your way.
For businesses throughout Florida, these benefits translate into real competitive advantages. Your customers choose businesses they trust with their data. Your operations stay running when competitors face disruptions. And your team focuses on growth instead of constantly putting out security fires.
At Smart Technologies of Florida, we’ve seen how regular network security audits transform security from a technical concern into a business asset that supports everything you’re working to build.
Common Vulnerabilities Identified in Network Security Audits
After conducting hundreds of network security audits for Florida businesses over our 23 years in operation, we’ve seen the same security issues appear time and again. Think of these as the “usual suspects” in the cybersecurity world. Understanding these common vulnerabilities can help you spot potential weaknesses before hackers do.

Misconfigured Firewalls
Your firewall is like your network’s front door—and we often find it’s been left partially open.
The problem isn’t usually that businesses don’t have firewalls, but rather that they’re not set up correctly. We regularly find overly permissive rules that allow unnecessary traffic through, essentially creating a welcome mat for potential intruders. Many organizations also maintain outdated rules that made sense years ago but now create security gaps.
“These rules are not static,” as security professionals often remind us. Your business changes, and your firewall configuration needs to change with it. Many companies set up their firewalls correctly initially but never revisit the settings as their business evolves.
Weak Passwords and Single-Factor Authentication
Despite all the warnings and headlines about breaches, password problems remain stubbornly common in our audits.
We still find default passwords that have never been changed (yes, really!), shared login credentials that multiple employees use, and passwords so simple they might as well be “password123.” What’s particularly concerning is how often we see weak passwords protecting the most sensitive parts of a business.
Industry research tells us human error is behind eight out of ten cyberattacks, with poor password habits being a major contributor. The good news? This vulnerability is relatively easy to fix with password managers and multi-factor authentication—small changes that create big security improvements.
Outdated Software and Missing Patches
One of the most preventable yet prevalent issues we find during network security audits is outdated software. This is like leaving your windows open uped in a neighborhood where everyone knows which locks are broken.
We regularly find operating systems missing critical security updates, applications running versions with known vulnerabilities, and worst of all, end-of-life software that no longer receives any security patches. The challenge is that many businesses don’t have a systematic approach to updates, leading to inconsistent patching across similar systems.
What makes this particularly dangerous is how quickly hackers move these days. The window between a patch release and exploitation is shrinking—sometimes to just hours. Your update strategy needs to keep pace with this accelerating threat landscape.
During our audits, we often surprise clients by showing them entry points to their network they didn’t even know existed.
These unauthorized access points take many forms: rogue wireless access points set up by well-meaning employees, forgotten legacy systems still connected to the network, improperly secured remote access tools, and unauthorized IoT devices quietly connecting to your network.
One memorable audit revealed a smart coffee maker that had been connecting to a client’s main network rather than their guest network—creating a potential entry point to sensitive financial data through their break room!
These unmanaged access points typically bypass your carefully planned security controls, creating direct paths for attackers to reach your most valuable resources.
Human Error and Lack of Awareness
The most sophisticated security technology in the world can’t protect you if your team doesn’t understand basic security practices.
During our audits, we frequently observe employees falling for simulated phishing attempts, sharing credentials when they shouldn’t, and bypassing security measures for convenience. In one case, we found sticky notes with passwords attached to monitors—in a financial services company!
Network security audits often reveal gaps not just in technology but in human understanding. The most resilient security approaches combine robust technical measures with ongoing security awareness training.
At Smart Technologies of Florida, we don’t just point out these vulnerabilities—we help you build practical, sustainable solutions that address both the technical and human elements of security. After all, knowing where the problems typically hide is the first step toward creating a truly secure business environment.
Automating Network Security Audits: Tools and Techniques
Remember when security audits meant clipboard-wielding IT folks manually checking every server in your building? Those days are thankfully behind us. As business networks have grown increasingly complex, trying to handle security audits manually has become like trying to count raindrops during a storm – technically possible but wildly impractical.
Today’s network security audit process leverages powerful automation tools that dramatically improve both efficiency and thoroughness. At Smart Technologies of Florida, we’ve seen how the right automation approach can transform security from a periodic headache into a continuous safeguard.

Automated Scanning and Monitoring
Think of automated scanning tools as tireless security guards that never need coffee breaks. These systems continuously patrol your network, identifying vulnerabilities that might go unnoticed in manual checks.
Modern vulnerability scanners can examine thousands of devices in the time it would take a human auditor to check just a handful. They’re constantly updated with the latest threat intelligence, meaning they can spot new vulnerabilities as they emerge in the wild. For our clients, this means comprehensive coverage without the massive time investment of traditional approaches.
Configuration management tools serve as another set of watchful eyes, alerting you when someone makes unauthorized changes to your systems. We’ve helped many Florida businesses implement these tools and watched them catch potentially serious security issues before they could cause harm.
Security Information and Event Management (SIEM)
If your network could tell its life story, SIEM would be the storyteller. These powerful systems gather logs from across your entire network – every device, application, and security control – and analyze them to identify patterns that might indicate security issues.
What makes SIEM solutions so valuable is their ability to connect the dots between seemingly unrelated events. That failed login attempt on your email server might not mean much on its own, but when the SIEM sees it happening alongside unusual network traffic and file access patterns, it can flag a potential attack in progress.
For businesses concerned about compliance, SIEM solutions are particularly valuable. They maintain comprehensive audit trails and can generate the reports you need to demonstrate regulatory compliance without hours of manual work.
Endpoint Detection and Response (EDR)
Your endpoints – computers, servers, mobile devices – are where the rubber meets the road in cybersecurity. They’re the front lines where users interact with data and applications, making them prime targets for attackers.
EDR solutions focus specifically on monitoring these crucial endpoints. They watch for unusual behaviors that might indicate compromise – like a workstation suddenly trying to access sensitive databases it’s never connected to before, or a server running processes that don’t match its normal patterns.
When we implement EDR for clients, they’re often surprised by how much visibility it provides. One Daytona Beach retailer finded an attempted data exfiltration within days of deployment – something their previous security measures had completely missed.
AI and Machine Learning Solutions
The newest frontier in security automation leverages artificial intelligence to boost your defenses. These systems don’t just look for known threats; they learn what’s normal for your specific network and flag anything that looks suspicious.
The beauty of AI-driven security tools is their ability to improve over time. With each alert they process and each response you provide, they get smarter about distinguishing between genuine threats and false alarms. This means your security team spends less time chasing ghosts and more time addressing real issues.
As one client put it after implementing AI security tools: “It’s like having a security analyst with perfect memory who never sleeps.” That’s the kind of advantage today’s businesses need in the face of increasingly sophisticated threats.
Network Policy as Code
For organizations embracing modern DevOps practices, “policy as code” approaches are changing how security is managed. Rather than maintaining separate security policies in documents that may or may not be followed, these organizations define their security requirements as code that can be automatically deployed and enforced.
This approach ensures consistent application of security standards across your environment and creates clear audit trails of policy changes. It’s particularly valuable for businesses with complex, rapidly changing environments where manual policy enforcement would be impractical.
The goal of automation isn’t to replace human expertise but to improve it. Your security team’s knowledge and judgment are still essential – automation simply frees them from routine tasks so they can focus on strategic issues that require human insight.
At Smart Technologies of Florida, we help our clients find the right balance of automation and human oversight for their specific needs. Every business is different, and there’s no one-size-fits-all approach to security automation. The key is implementing tools that address your particular risks and integrate smoothly with your existing processes.
Compliance and Regulatory Requirements
Meeting regulatory requirements isn’t just a legal checkbox—it’s often the primary motivation behind conducting a network security audit in the first place. Understanding which regulations apply to your business is essential for both staying on the right side of the law and protecting your valuable data.
Key Regulatory Frameworks
The regulatory landscape can feel like alphabet soup, but each framework serves an important purpose. Let’s break down the major ones that might affect your Florida business:
GDPR (General Data Protection Regulation) has changed how businesses worldwide handle personal data. If you serve customers in the EU (even as a Florida-based company), GDPR applies to you. This regulation demands comprehensive data protection measures and requires you to report breaches within 72 hours—a timeline that feels impossibly short without proper preparation. The penalties are attention-grabbing too: up to 4% of your global revenue for serious violations.
HIPAA (Health Insurance Portability and Accountability Act) is the cornerstone of healthcare data protection. For medical practices, hospitals, and even their business partners, HIPAA compliance isn’t optional. Beyond protecting patient information, HIPAA requires regular risk assessments—essentially mandating ongoing network security audits as part of normal operations.
PCI DSS (Payment Card Industry Data Security Standard) affects virtually every retail business. If you accept credit cards (and who doesn’t these days?), you need to comply with PCI DSS requirements. This means maintaining secure networks, regularly testing for vulnerabilities, and implementing strict access controls. A network security audit helps identify gaps in your payment processing security before they lead to a breach.
NIST Cybersecurity Framework may be voluntary, but it’s widely respected and increasingly referenced in contracts and insurance policies. This framework provides a structured approach to security through five core functions: Identify, Protect, Detect, Respond, and Recover. It’s flexible enough to work for small Florida businesses and large enterprises alike.
ISO 27001 offers an international standard for information security management. While adoption is voluntary, certification can demonstrate to clients and partners that you take security seriously. The standard requires establishing a systematic approach to managing sensitive information and conducting regular internal audits—making it a natural fit with ongoing network security audit programs.
| Compliance Standard | Key Requirements | Potential Penalties |
|---|---|---|
| GDPR | Data protection, breach notification, privacy rights | Up to €20M or 4% of global revenue |
| HIPAA | PHI protection, access controls, risk assessments | Up to $1.5M per violation category annually |
| PCI DSS | Secure processing, scanning, access restrictions | $5,000-$100,000 monthly fines, increased transaction fees |
| NIST | Risk-based approach, continuous monitoring | No direct penalties (contractual implications) |
| ISO 27001 | ISMS implementation, regular audits | No direct penalties (certification loss) |
Compliance-Focused Auditing
When your network security audit needs to satisfy regulatory requirements, the approach shifts slightly. You’ll need to map your audit activities directly to specific compliance controls, maintain detailed documentation as evidence, and develop remediation plans that prioritize compliance gaps.
The good news? A well-designed audit can address multiple compliance frameworks simultaneously. At Smart Technologies of Florida, we’ve helped countless businesses streamline their compliance efforts by designing audit processes that satisfy overlapping requirements from different regulations. This integrated approach saves time and resources while ensuring comprehensive coverage.
Compliance as a Baseline, Not a Ceiling
Here’s something we tell all our clients: meeting regulatory requirements doesn’t guarantee security. As the saying goes in cybersecurity circles, “Compliance is where security begins, not where it ends.”
Think of compliance like the minimum speed on a highway—it keeps you from getting a ticket, but sometimes you need to go faster to keep up with traffic. Similarly, regulations establish minimum standards that may not address your specific risks or the latest threats.
The most effective approach combines compliance requirements with a clear-eyed assessment of your unique risk profile. This balanced strategy ensures you’re protected both legally and practically against today’s increasingly sophisticated cyber threats.
At Smart Technologies of Florida, we’ve spent 23 years helping businesses steer the complex intersection of compliance and security. Our people-centric approach ensures that your network security audit not only checks the regulatory boxes but also provides meaningful protection for your business’s most valuable assets.
Challenges in Network Security Audits and How to Overcome Them
Running a network security audit isn’t always smooth sailing. Even with the best plans in place, most organizations hit a few roadblocks along the way. The good news? These challenges aren’t impossible – they’re just part of the journey toward better security.
Resource Constraints
Let’s face it – not every business has unlimited funds, time, or people to throw at security audits. When you’re juggling multiple priorities, security can sometimes take a backseat.
At Smart Technologies of Florida, we’ve seen this challenge time and again with our clients. The solution isn’t necessarily more resources, but smarter use of what you have. Prioritizing your most critical systems based on risk is often the best place to start. You might not be able to audit everything at once, but you can make sure your crown jewels get the attention they deserve.
Automation tools can also be game-changers here. They won’t replace human expertise, but they can handle repetitive scanning tasks while your team focuses on analysis and remediation. Consider breaking your audit into phases if a comprehensive assessment feels overwhelming – security improvement is a marathon, not a sprint.
Network Complexity
Today’s networks are a far cry from the simple setups of the past. With a mix of on-premise systems, cloud services, remote workers, and IoT devices, getting a complete picture can feel like assembling a thousand-piece puzzle in the dark.
The foundation of tackling complexity is knowing what you have. Clear network diagrams and thorough asset inventories are worth their weight in gold during an audit. Automated findy tools can help ensure nothing slips through the cracks – we’ve had clients find devices they didn’t even know were connected to their networks!
For particularly complex environments, breaking your network security audit into segments (cloud infrastructure one month, on-premise systems the next) can make the process more manageable without sacrificing thoroughness.
Skills Shortage
Cybersecurity talent is in high demand and short supply. Finding people who understand both the technical nuts and bolts and proper audit methodology can feel like searching for unicorns.
This is where investing in your existing team often pays dividends. Training programs and security certifications can help bridge knowledge gaps, while standardized audit procedures make it easier to share responsibilities across team members with different expertise levels.
For specialized assessments, don’t be afraid to bring in outside help. At Smart Technologies of Florida, we often serve as an extension of our clients’ teams, providing specialized skills for specific audit components without the need for full-time hires.
Rapidly Evolving Threats
The security landscape changes at breakneck speed. What was secure yesterday might be vulnerable today, making it challenging to keep audit standards current.
Staying informed is your best defense. Threat intelligence services provide early warnings about emerging vulnerabilities, while participation in industry information-sharing groups helps you learn from others’ experiences before facing the same challenges yourself.
Rather than treating security as a once-a-year event, consider implementing more frequent, focused assessments of your highest-risk areas. This approach helps you stay ahead of evolving threats without overwhelming your team.
Organizational Resistance
Let’s be honest – nobody likes being audited. Departments might drag their feet or even actively resist, fearing disruption or worrying that findings will reflect poorly on their work.
The key to overcoming resistance is changing the narrative. Network security audits aren’t about catching people doing something wrong; they’re about protecting the organization’s future. When we work with clients at Smart Technologies of Florida, we emphasize that audits are protective, not punitive.
Involving stakeholders early in the planning process helps address concerns proactively and builds buy-in. Focus on constructive recommendations rather than assigning blame, and take time to demonstrate how security improvements support business goals.
Legacy Systems
Those old systems that “just work” often become security headaches during audits. They may lack modern security features or be incompatible with your automated tools.
When facing legacy challenges, creativity becomes essential. Custom audit procedures might be needed for systems that can’t be assessed with standard tools. Where direct fixes aren’t possible, compensating controls can help reduce risk – for example, implementing stronger network segmentation around vulnerable legacy systems.
For particularly problematic legacy systems, developing a migration roadmap might be the best long-term solution, even if immediate replacement isn’t feasible.
At Smart Technologies of Florida, we’ve helped businesses throughout Daytona Beach and across Florida steer these challenges for over two decades. Our people-centric approach recognizes that successful network security audits require addressing both technical and human factors. With the right strategies, these common roadblocks become manageable steps on your journey to stronger security.
Preparing for a Network Security Audit
Getting ready for a network security audit doesn’t have to feel like preparing for a dreaded inspection. Think of it more like getting your house in order before having important guests over—a little preparation goes a long way toward making the experience positive and productive.
Assemble the Right Team
Every successful audit starts with bringing together the right people. You’ll need your IT experts who know the technical details, business managers who understand day-to-day operations, and perhaps compliance specialists who can speak to regulatory requirements. Don’t forget to include an executive sponsor who can help clear roadblocks and provide necessary resources.
Having this diverse team ensures your audit considers both hardcore security needs and practical business realities. After all, security solutions that don’t work with your business processes won’t get used, no matter how technically sound they are.
Gather Documentation
Before your audit begins, take time to collect and organize key documentation. This might feel tedious, but it’s like having your medical records ready before a doctor’s appointment—it makes everything more efficient.
Pull together your network diagrams, asset inventories, security policies, and previous audit reports. Don’t forget about incident response plans and change management logs too. Having these materials organized and accessible saves everyone time and helps auditors understand your environment more thoroughly.
I’ve seen many audits delayed simply because basic documentation wasn’t readily available. One client told me they spent more time hunting down network diagrams than they did on the actual audit work!
Communicate with Stakeholders
Clear communication prevents the anxiety and resistance that often accompany security audits. Be upfront with your team about what’s happening, why it matters, and how the process will unfold.
Explain that the audit isn’t about finding fault or placing blame—it’s about strengthening your defenses before the bad guys find weaknesses. When people understand that a network security audit is protective rather than punitive, they’re much more likely to participate constructively.
Share the timeline, resource needs, and how findings will be handled. This transparency builds trust and cooperation throughout the process.
Conduct a Pre-Audit Assessment
Before the formal audit begins, do a quick self-check of obvious security issues. This is like tidying up before the professional cleaners arrive—it lets the experts focus on the deeper work.
Take a look at known security issues you haven’t yet addressed. Verify that basic security practices like patch management are being followed. Make sure your security tools are working properly and that auditors will have appropriate access to the systems they need to evaluate.
This preliminary assessment often catches the low-hanging fruit, allowing the actual audit to dig into more complex security challenges.
Establish a Findings Management Process
Decide in advance how you’ll handle audit findings. Without a clear process, even the best audit insights can end up collecting dust instead of improving security.
Determine who will receive the findings, how you’ll prioritize issues for fixing, what system you’ll use to track remediation efforts, and when you’ll verify that problems have been properly addressed. Having this workflow established makes the transition from finding problems to fixing them much smoother.
At Smart Technologies of Florida, we’ve spent 23 years helping businesses prepare for and conduct security audits. We’ve learned that this preparation phase often determines whether an audit delivers real value or becomes just another compliance checkbox. A well-prepared organization not only gets more accurate results but is better positioned to act effectively on what they learn.
The goal isn’t just to pass an audit—it’s to genuinely strengthen your security posture and protect your business from evolving threats.
Frequently Asked Questions about Network Security Audits
How often should a network security audit be performed?
When it comes to the timing of network security audits, there’s no one-size-fits-all answer. Think of it like your car’s maintenance schedule – the frequency depends on how you use it, where you drive, and what kind of vehicle you have.
For most businesses, an annual comprehensive audit serves as a solid foundation. This yearly check-up gives you a thorough assessment of your security posture and helps identify any developing issues before they become serious problems.
However, certain systems might need more frequent attention. Your most critical systems – those handling sensitive customer data or financial information – often benefit from quarterly targeted assessments. These focused reviews help ensure your most valuable assets remain well-protected throughout the year.
Between these scheduled check-ups, continuous monitoring acts like your security dashboard warning lights, alerting you to potential issues in real-time. This ongoing vigilance has become increasingly important in today’s rapidly evolving threat landscape.
Perhaps most importantly, you should conduct additional audits whenever significant changes occur in your environment. Just added a new cloud service? Implemented a major system upgrade? Restructured your network? These moments of change often create unexpected security gaps that need immediate attention.
For businesses in heavily regulated industries like healthcare or finance, regulatory requirements might dictate more frequent audits. As one security expert puts it, “Audits should be performed immediately after major network changes, security incidents, or new compliance requirements.” This event-based approach works alongside your regular audit schedule to provide comprehensive protection.
Who should conduct a network security audit?
Choosing who performs your network security audit is a bit like deciding whether to change your own oil or take your car to a mechanic – it depends on your expertise, resources, and how complex the job is.
Internal teams bring valuable insider knowledge to the table. They understand your systems, know your business processes, and can often conduct assessments at a lower direct cost. Your internal staff can also perform more frequent checks since they’re already on the payroll. However, they might lack specialized expertise for complex assessments, and there’s always the challenge of objectivity – it’s hard to critically evaluate systems you’ve helped build and maintain.
External specialists, on the other hand, bring fresh eyes and specialized expertise. They see things your team might miss simply because they’re not accustomed to your environment. External auditors also bring broader experience from working with multiple organizations, often identifying issues based on patterns they’ve seen elsewhere. The downside? Higher direct costs and a learning curve as they get up to speed on your unique environment.
Many of our clients at Smart Technologies of Florida find that a combined approach works best. Your internal team handles routine assessments and daily monitoring, while we step in periodically to provide comprehensive audits or specialized assessments that require specific expertise.
This collaborative approach gives you the best of both worlds – your team’s deep institutional knowledge paired with our external perspective and specialized security expertise. After 23 years of helping Florida businesses secure their networks, we’ve found this partnership model consistently delivers the most value.
What is the difference between a vulnerability scan and a penetration test?
Understanding the difference between vulnerability scanning and penetration testing is crucial when planning your network security audit strategy. Though they’re often mentioned together, they serve very different purposes in your security program.
A vulnerability scan is like having a home inspector check all your doors and windows to see if they’re properly locked. It’s an automated process that systematically checks your systems for known security weaknesses – missing patches, outdated software, misconfigured settings, and common security flaws. These scans are relatively non-intrusive and can be run frequently (weekly or monthly) without disrupting your operations. They provide broad coverage of your environment but don’t dive deeply into how vulnerabilities might be exploited.
A penetration test, by contrast, is like hiring a professional locksmith to actually try breaking into your building. It’s an active attempt to exploit vulnerabilities to assess real-world risk. Skilled security professionals think like attackers, attempting to breach your defenses and seeing how far they can get once inside. Penetration tests are more intrusive and typically performed less frequently – annually or semi-annually for most organizations. They provide deep insights but focus on specific areas rather than your entire network.
As one security professional explains it, “Vulnerability scanning tells you where your doors and windows are left open, while penetration testing shows you how an intruder might actually break in and what they could access once inside.”
A robust security program needs both approaches. Regular vulnerability scanning helps you maintain good security hygiene by identifying and fixing common weaknesses before attackers can exploit them. Periodic penetration testing reveals more subtle vulnerabilities and helps you understand the real-world impact of security gaps when exploited by a determined attacker.
At Smart Technologies of Florida, we help our clients implement both strategies in a balanced approach that maximizes protection while respecting budget constraints. The right mix depends on your specific business needs, regulatory requirements, and risk tolerance – something we’re happy to help you determine.
Conclusion
In today’s rapidly evolving threat landscape, a robust network security audit program is no longer optional—it’s essential for business survival. The digital world presents both opportunities and dangers, and the businesses that thrive are those that understand and manage their security risks proactively.
Throughout this guide, we’ve explored how regular audits provide the visibility and insights needed to protect your critical assets from increasingly sophisticated cyber threats. The evidence speaks for itself: with businesses facing over 1,636 cyberattacks weekly and data breaches costing an average of $4.88 million, investing in security isn’t just a technical decision—it’s a business imperative.
Think of security audits as regular health checkups for your digital infrastructure. Just as you wouldn’t wait for a major health crisis before seeing a doctor, you shouldn’t wait for a breach to assess your network security. Prevention is always less painful and less expensive than recovery.
At Smart Technologies of Florida, we’ve spent 23 years helping businesses in Daytona Beach and throughout Florida develop effective security strategies that work in the real world. Our people-centric approach means we don’t just focus on technology—we ensure that security measures align with your unique business goals and operational needs. We understand that the most sophisticated security tools are worthless if they disrupt your ability to serve customers or grow your business.
Security is a journey, not a destination. The cyber threat landscape continues to evolve, and your security program must evolve with it. Regular network security audits provide the feedback mechanism needed to ensure your defenses remain effective against emerging threats.
By following the structured approach outlined in this guide—from defining audit scope and inventorying assets to implementing remediation measures and continuous monitoring—you can significantly reduce your organization’s risk exposure. This methodical approach also demonstrates due diligence to customers, partners, and regulators who increasingly expect businesses to take security seriously.
Don’t wait for a breach to reveal your vulnerabilities. The most successful businesses are taking proactive steps today to secure their operations for tomorrow. Your business has worked too hard to build its reputation and customer trust to let preventable security issues put everything at risk.
Whether you’re just beginning your security journey or looking to improve an existing program, we’re here to help you steer the complexities of modern cybersecurity with practical, business-focused solutions.












