Network Security Solutions 101
Network security solutions are specialized tools and technologies designed to protect your business’s digital infrastructure from cyber threats, data breaches, and unauthorized access. With cybercrime on the rise, implementing the right security measures is no longer optional—it’s essential for survival.
Key solutions for modern businesses include Next-Generation Firewalls (NGFW), Zero Trust Network Access (ZTNA), and Secure Access Service Edge (SASE), which provide advanced protection far beyond traditional methods.
While cybersecurity is a broad term covering all digital assets (endpoints, applications, cloud services), network security specifically focuses on protecting your network infrastructure and the data flowing through it.
Today’s businesses face a threat landscape where old security tools are obsolete. This guide will walk you through the core principles of network security, the types of solutions available, and how to implement a comprehensive strategy that protects your business while enabling growth.
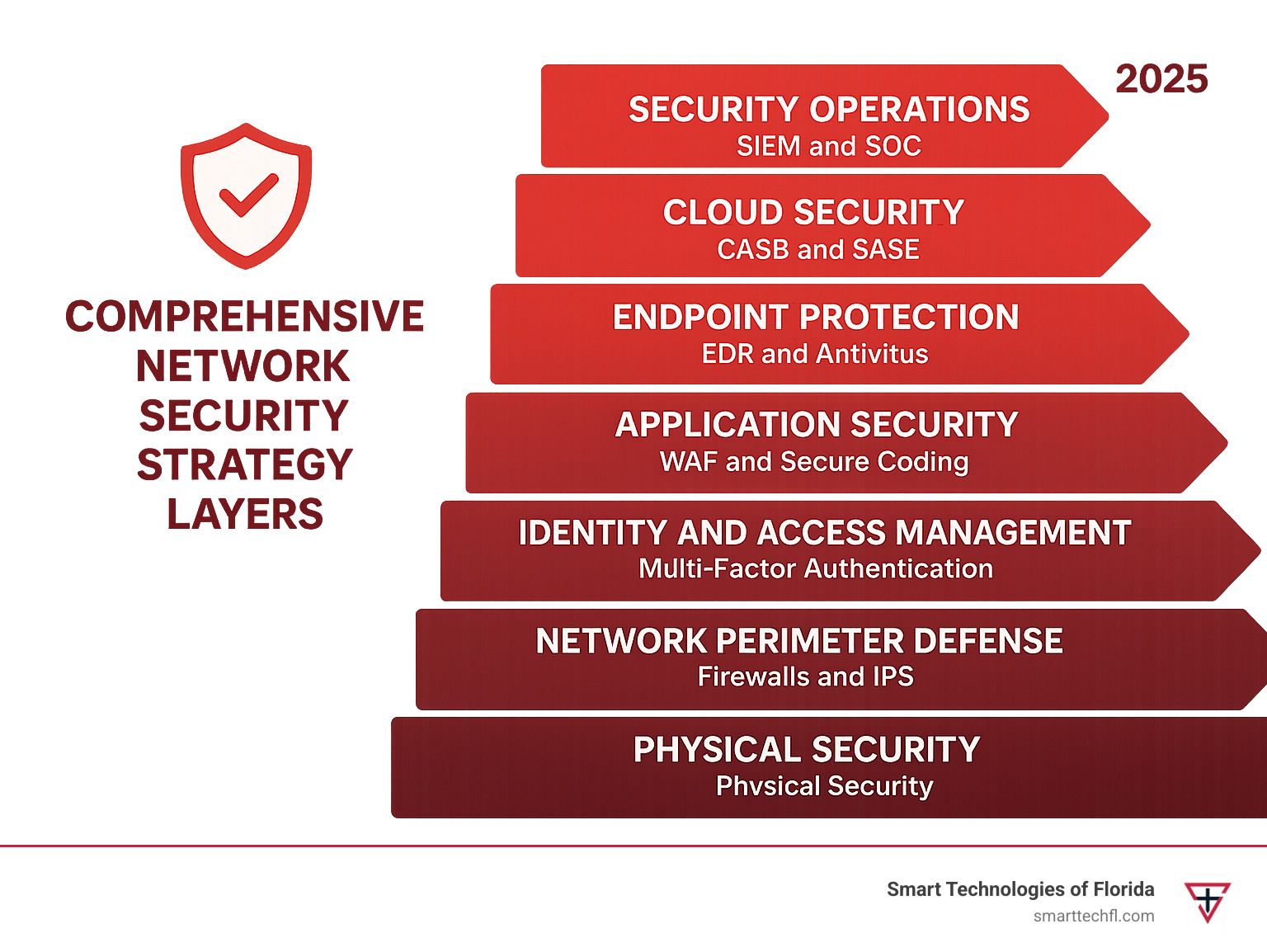
Understanding the Core Principles of Network Security
An effective network security strategy rests on three fundamental pillars: Protection, Detection, and Response. These principles work together to create a resilient defense against cyber threats.

- Protection: This is your first line of defense, involving proactive measures like access controls and threat prevention systems to stop attacks before they can cause damage.
- Detection: Since no protection is perfect, continuous monitoring is crucial. This pillar focuses on identifying unusual activity or suspicious behavior that might indicate a breach. Our Real-Time Threat Detection services ensure nothing goes unnoticed.
- Response: When a threat is detected, a swift and decisive response is critical. A well-defined plan contains the threat quickly, minimizes damage, and restores normal operations. Our Breach Analysis Prevent Cyber Attacks approach helps businesses recover rapidly.
How Security Solutions Protect Your Network
Modern network security solutions use a combination of technologies to safeguard your digital assets. Key components include:
- Access Control: Determines who can access your network and what they are authorized to do, enforcing the principle of least privilege.
- Authentication: Verifies user identities, often through multi-factor authentication (MFA), to ensure only legitimate users gain access.
- Encryption: Scrambles data into an unreadable format, protecting it both in transit and at rest from unauthorized viewing.
- Firewalls: Act as gatekeepers, monitoring and controlling incoming and outgoing network traffic based on predefined security rules.
- Intrusion Prevention Systems (IPS): Actively scan network traffic for malicious activity and automatically block identified threats.
- Data Loss Prevention (DLP): Prevents sensitive information from leaving the network without authorization, helping to stop data breaches and insider threats.
Understanding the Anatomy of a Cyberattack highlights why these solutions must work together as a unified system.
The Importance of a Layered Defense (Defense in Depth)
No single security tool is foolproof, which is why a defense in depth strategy is essential. This approach involves creating multiple, overlapping layers of security controls throughout your network. If one layer fails, others are in place to stop the attack.
A layered defense eliminates single points of failure, creates a proactive security posture by catching threats at different stages, and helps reduce your attack surface by isolating critical systems. Each additional layer increases the difficulty for an attacker, raising their risk of detection and failure. Our approach to Vulnerability Risk Management for Business is built on this philosophy of comprehensive, multi-layered protection.
A Deep Dive into the Types of Network Security Solutions
The world of network security solutions has evolved from simple firewalls to a sophisticated ecosystem of tools for on-premise, cloud, and hybrid environments. With more than 50% of incidents expected to come from cloud network activity by 2029, modernizing your security strategy is critical.
Effective protection doesn’t require a massive budget. Our Cybersecurity Solutions for Small Business show that strategic choices can deliver enterprise-level security.
Foundational Security Tools
These are the essential building blocks of any security posture:
- Next-Generation Firewalls (NGFW): Unlike traditional firewalls, NGFWs inspect traffic at the application layer, identifying malicious activity hidden within legitimate-looking data. They often include built-in intrusion prevention and threat intelligence.
- Virtual Private Networks (VPN): Create encrypted tunnels for secure remote access. While still useful, traditional VPNs often grant overly broad network access, which can be a risk in modern, distributed work environments.
- Network Access Control (NAC): Ensures only authorized and compliant devices can connect to your network. NAC is vital for managing corporate and personal devices (BYOD) and meeting compliance mandates.
- Web Application Firewalls (WAF): Provide specialized Layer 7 protection for your web applications and websites against attacks like SQL injection and cross-site scripting.
- Secure Web Gateways (SWG): Monitor internet usage to block malicious websites, prevent malware downloads, and enforce acceptable use policies.
- Email Security: Effective Email Spam Filters Boost Security by blocking phishing attempts and malicious attachments at the perimeter.
Advanced and Modern Network Security Solutions
As threats evolve, so must our defenses. These solutions represent the cutting edge of network protection:
- Zero Trust Network Access (ZTNA): Operates on a “never trust, always verify” principle. Access to resources is granted on a per-session basis after strict verification, creating micro-perimeters that limit lateral movement for attackers.
- Network Segmentation and Microsegmentation: Divides the network into smaller, isolated zones. Microsegmentation takes this further by creating granular zones around critical assets, containing breaches if they occur.
- Secure Access Service Edge (SASE): A cloud-native framework that combines networking (SD-WAN) and security services (like ZTNA and SWG) into a single, unified platform, ideal for distributed workforces.
- Extended Detection and Response (XDR): Correlates data from across your entire IT environment (endpoints, network, cloud) to provide a holistic view and detect sophisticated, multi-stage attacks.
- Network Detection and Response (NDR): Uses AI and machine learning to analyze network traffic for anomalous behavior, spotting emerging threats that may not have a known signature.
These advanced tools are the core of modern Threat Detection and Response Systems, enabling businesses to adapt to a fast-changing threat landscape.
Building and Implementing Your Comprehensive Security Strategy
An effective network security solutions strategy requires a personalized approach custom to your organization’s unique needs, risks, and goals.

The process begins with a thorough assessment phase:
- Business Needs & Risk Assessment: Identify your most critical systems and data to understand the potential impact of an attack. This drives every security decision.
- Asset Identification: You can’t protect what you don’t know you have. Map all servers, workstations, mobile devices, and cloud services to identify potential entry points.
- Regulatory Compliance: Ensure your strategy meets legal and industry requirements like HIPAA, PCI DSS, or GDPR. The Cybersecurity Framework developed by NIST provides an excellent foundation.
Our Network Security Audit Guide can help establish a baseline and identify priorities.
The Role of AI in Modern Security
Artificial Intelligence is changing network security solutions by enabling proactive and automated defense.
- AI-Powered Threat Detection: AI goes beyond signature-based tools to spot suspicious patterns and behaviors that indicate novel or advanced threats.
- Behavioral Analytics (UEBA): Establishes a baseline of normal network activity to instantly flag deviations, which is highly effective for catching insider threats or compromised accounts.
- Automated Incident Response: AI can instantly isolate infected devices or block malicious connections, dramatically reducing response times and containing threats like ransomware before they spread.
- Predictive Analysis: By analyzing global threat data, AI can help predict emerging attack patterns, allowing organizations to prepare their defenses in advance. The Future of Automated Threat Detection relies heavily on these capabilities.
Best Practices for Implementing and Maintaining Your Network Security Solutions
Implementation is just the start. Ongoing maintenance is crucial for long-term protection.
- Regular Security Audits: Periodically assess your defenses to identify weaknesses and ensure controls are working as intended.
- Continuous Monitoring: Cyber threats don’t sleep, so your network requires 24/7 monitoring of traffic, logs, and user activity.
- Employee Security Awareness Training: Turn your staff into a line of defense by training them to recognize phishing, social engineering, and other common tactics.
- Patch Management: Consistently apply security patches to all systems and applications to close known vulnerabilities that attackers exploit.
- Incident Response Planning: Develop and test a clear plan for what to do when a breach occurs to ensure a swift and effective response.
Our IT Consulting Services can help you establish and maintain these critical practices.
How to Choose the Right Solution for Your Business
Selecting the right network security solutions is about finding the best fit for your unique business needs, not just buying the most feature-rich product. The best solution is one that aligns with your specific risks, budget, and operational requirements.
Here are the key factors to consider when making your decision:
- Mapping Requirements to Features: Start by identifying your most critical assets and biggest risks. Then, evaluate solutions based on how well their features address those specific needs. Avoid paying for advanced capabilities you won’t use.
- Scalability and Performance: The solution must grow with your business without slowing down operations. Test for low latency and high throughput to ensure security doesn’t create bottlenecks for your team.
- Budget and Total Cost of Ownership (TCO): Look beyond the initial price tag. Consider ongoing costs for maintenance, administration, and training. An integrated solution can sometimes be more cost-effective than managing multiple disparate tools.
- Ease of Management and Integration: A complex solution can lead to misconfigurations. Prioritize tools with intuitive interfaces that integrate smoothly with your existing infrastructure to minimize disruption and human error.
- User Experience (UX): Security should be as seamless as possible. If a tool is too intrusive, employees may seek workarounds that create new vulnerabilities. A positive UX encourages compliance and strengthens your overall security posture.
- Vendor Support and Future-Proofing: Choose a vendor with a reputation for reliable support and continuous innovation. The threat landscape evolves quickly, so your solution must adapt with regular updates and new capabilities.
Our Managed Network Security Solutions can help you steer these decisions, while a strategic Business Technology Upgrade is an ideal time to reassess your security posture.
Frequently Asked Questions about Network Security
Here are answers to common questions about network security solutions.
What is the difference between network security and cybersecurity?
Cybersecurity is the broad practice of protecting all digital assets, including computers, applications, cloud services, and data. Network security is a specific subset of cybersecurity focused on protecting the network infrastructure itself—the pathways that connect your systems and through which data flows.
Are traditional firewalls obsolete?
Yes, for the most part. Traditional firewalls only inspect basic information like IP addresses and ports, making them ineffective against modern attacks that hide within legitimate-looking traffic. Next-Generation Firewalls (NGFWs) are the current standard because they provide application-layer inspection, allowing them to understand the context of the data and identify sophisticated threats. This is especially critical in dynamic cloud environments.
What is a Zero Trust security model?
Zero Trust is a security framework built on the principle of “never trust, always verify.” It eliminates the outdated idea of a trusted internal network. Instead, every user and device must be strictly authenticated and authorized for every resource they attempt to access, every single time. This model also enforces least-privilege access, giving users only the minimum access required for their jobs. This dramatically reduces the potential damage from a breach by limiting an attacker’s ability to move laterally within the network.
Conclusion
A proactive, layered security strategy is a fundamental requirement for business survival and growth. The right network security solutions—from foundational NGFWs to advanced frameworks like Zero Trust and SASE—protect your critical assets and enable your business to thrive in an evolving threat landscape.
Effective security is not about buying every tool, but about implementing a thoughtful strategy that aligns with your specific business needs, risks, and goals. Modern solutions powered by AI make it possible to achieve strong security without sacrificing productivity.
At Smart Technologies of Florida, our people-centric approach, refined over 23 years, empowers organizations through strategic innovation. We help you build a security posture that acts as a business enabler, giving you the confidence to grow.
Don’t let complexity be a barrier. Take control of your network security today to turn potential vulnerabilities into a competitive advantage.
Get expert help with your managed IT solutions and build a resilient security foundation for your business.












