The Complete Guide to Understanding Email Filtering
Email filtering is the automated process of sorting, blocking, and organizing incoming and outgoing emails based on predefined security and business rules. Here’s what you need to know:
Key Components:
- Spam Detection – Blocks unwanted bulk emails automatically
- Phishing Protection – Identifies and quarantines malicious emails trying to steal data
- Malware Scanning – Catches viruses and dangerous attachments before they reach inboxes
- Data Loss Prevention – Monitors outgoing emails to prevent sensitive information leaks
- Content Organization – Automatically sorts emails into folders based on sender, subject, or content
Why It Matters for Your Business:
- Protects against cyber threats that cost businesses thousands in damages
- Reduces inbox clutter so employees focus on important messages
- Ensures compliance with industry regulations
- Prevents accidental data breaches through outbound monitoring
With 45% of all emails being spam and cybercriminals increasingly using email as their primary attack vector, effective filtering isn’t optional anymore—it’s a business necessity.
The challenge isn’t just volume. Modern threats are sophisticated. Phishing emails look legitimate. Malware hides in everyday attachments. Your team needs protection that works before these threats reach their inboxes.
That’s where smart email filtering comes in. It acts as your digital security guard, checking every message against known threats while learning your business’s unique email patterns.
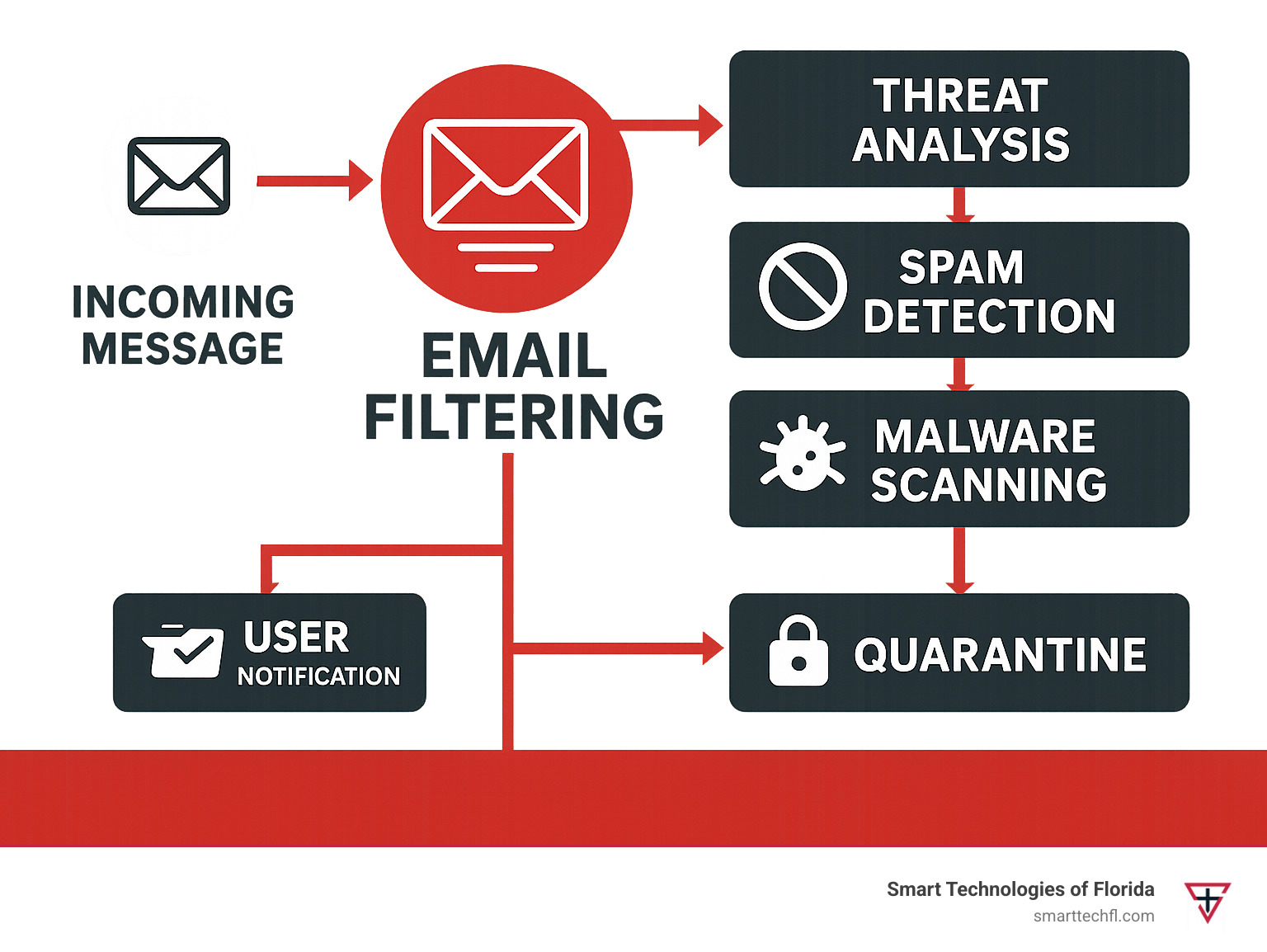
What is Email Filtering?
Imagine having a personal assistant who checks every piece of mail before it reaches your desk. They sort the important letters, toss the junk, and flag anything suspicious. That’s exactly what email filtering does for your digital mailbox—it’s an automated sorting system that makes smart decisions about every email flowing through your organization.
Email filtering works by examining each message like a detective looking for clues. It checks the sender’s reputation to see if they’re trustworthy. It scans the content for suspicious keywords or patterns that scream “scam alert.” The system inspects attachments for hidden dangers and verifies that embedded links won’t send you to malicious websites. Most importantly, it confirms whether the sender is actually who they claim to be.
Based on what it finds, the filter takes action according to your rules. Clean emails go straight to your inbox. Questionable ones might land in your spam folder. Really suspicious messages get quarantined for human review, while the worst offenders are blocked entirely.
But modern email filtering isn’t just about stopping obvious spam anymore. It’s become much smarter, handling three distinct types of unwanted email. Spam filtering blocks those classic “get rich quick” schemes and random promotions that waste everyone’s time. Graymail filtering manages the trickier stuff—emails you technically signed up for but never actually read, like that newsletter from a store you visited once. Most critically, phishing protection catches sophisticated attempts to steal your passwords, install malware, or trick your employees into wiring money to criminals.
The beauty of today’s systems is how they enforce your organization’s email policies automatically. They prevent data leaks by scanning outgoing messages for sensitive information. They keep your mailboxes organized by sorting emails into appropriate folders. And they help you meet regulatory requirements without adding extra work to your team’s day.
History & Evolution of Email Filtering
Email filtering started simple—almost embarrassingly so. Early systems were like overeager security guards who only knew how to look for obvious troublemakers. They’d scan for keywords like “FREE MONEY” in subject lines and call it a day. If spammers got creative with their spelling, these filters were stumped.
The real game-changer came with SpamAssassin, an open-source project that introduced something revolutionary: scoring systems. Instead of simple yes-or-no decisions, it treated spam detection like grading a test. Each suspicious element added points, and only emails with high scores got blocked. This approach was far more nuanced and effective.
Then came the Bayesian breakthrough that transformed everything. These statistical filters were like having a system that actually learned your preferences. They studied your email patterns and built personalized models of what looked like spam versus legitimate mail for each user. The more you used them, the smarter they became at recognizing your unique email habits.
The 2010s brought us cloud-based gateways that changed the scale entirely. Suddenly, systems could process millions of emails simultaneously while sharing threat intelligence across all customers. When one organization received a new phishing campaign, every other customer was protected within minutes. It was like having a neighborhood watch program for the entire internet.
Today, we’re living in the AI and Large Language Model era. Modern filters understand context in ways that seemed impossible just a few years ago. They can detect AI-generated phishing content, analyze subtle sender behavior patterns, and even catch threats at the SMTP stage before they fully enter your system. It’s sophisticated stuff that would make those early keyword filters look like stone tools.
Core Concepts & Terminology
Getting comfortable with email filtering means understanding the language that comes with it. Don’t worry—it’s not as complicated as it sounds.
Your allowlist (sometimes called a whitelist) is your VIP list of trusted senders. These are the good guys—your bank, key business partners, or that one vendor who always sends important updates. Their emails sail straight through to your inbox, no questions asked.
On the flip side, your blocklist (or blacklist) contains the troublemakers. These are known bad actors whose emails get automatically deleted or quarantined. Think of it as your “do not admit” list for digital bouncers.
When an email lands in quarantine, it’s like being held in a waiting room. The system isn’t sure if it’s good or bad, so it holds the message for human review. This prevents potentially important emails from disappearing while keeping suspicious ones away from your inbox.
The score threshold is your system’s decision point—a numerical cutoff that determines spam versus legitimate mail. If an email scores above your threshold (say, 5.0 points), it gets blocked. Below that, it gets delivered. Finding the right balance is crucial for avoiding false positives—legitimate emails incorrectly flagged as spam. These are every administrator’s nightmare because they can block important business communications.
False negatives are the opposite problem—spam that sneaks through to your inbox. They’re annoying but less dangerous than missing legitimate emails.
RBLs (Reputation Block Lists) work like shared databases of known troublemakers. When IP addresses or domains get caught sending spam, they’re added to these lists that all filter systems can reference.
Finally, DMARC, SPF, and DKIM are the email world’s version of ID verification. These authentication protocols help confirm that senders are actually who they claim to be, making it much harder for criminals to impersonate your trusted contacts.
How Email Filtering Works – Inbound & Outbound Pipelines
Think of email filtering as your organization’s digital security checkpoint—but instead of checking bags at an airport, it’s examining every email that tries to enter or leave your network. The process is surprisingly sophisticated, happening in milliseconds while you’re completely unaware.
The magic starts before the email even arrives. During the SMTP handshake—basically a digital “hello” between mail servers—your filter is already checking the sender’s reputation. If that IP address has been sending spam, the conversation ends right there.
Once the connection is approved, header analysis kicks in. Every email carries routing information like a postal envelope, and filters examine this metadata for signs of tampering or spoofing. Legitimate emails follow predictable patterns, while malicious ones often show telltale inconsistencies.
Content scanning is where things get really interesting. The filter analyzes the message body, attachments, and embedded links using multiple techniques. It’s looking for suspicious keywords, unusual formatting, and social engineering tactics that humans might miss.
Reputation lookup happens simultaneously, cross-referencing the sender against multiple threat intelligence databases. The system considers factors like sending volume, complaint rates, and historical behavior to build a trust score.
For suspicious attachments, sandbox detonation provides the ultimate test. The filter executes files in isolated virtual environments, watching their behavior like a scientist observing bacteria in a petri dish. If the file tries to steal data or install malware, it never reaches your inbox.
DLP triggers scan outbound emails for sensitive information patterns—credit card numbers, social security numbers, or confidential documents that shouldn’t leave your organization. Meanwhile, encryption checks ensure that sensitive communications meet your security requirements.
Inbound Email Filtering
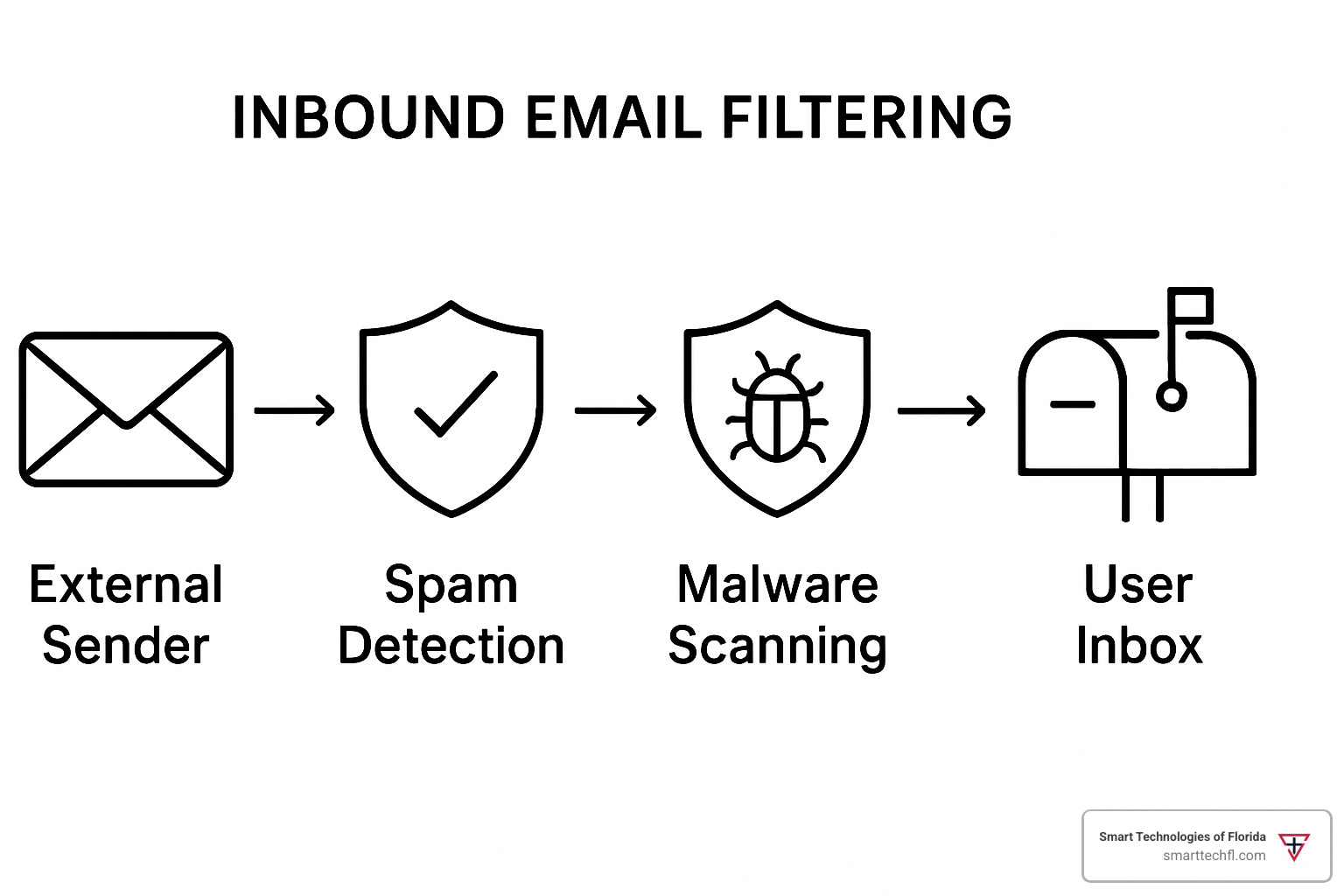
Your email filtering gateway is like having a really smart bouncer at the front door of your digital office. When an email arrives, it goes through multiple security layers that work together seamlessly.
Reputation-based filtering happens first. The system checks the sender’s IP address and domain against databases of known troublemakers. If someone has a history of sending spam or malware, their message gets flagged immediately—no questions asked.
Header analysis examines the email’s digital passport. Every email carries routing information showing where it’s been, and legitimate messages follow predictable paths. Malicious emails often show inconsistencies that give away their true intentions.
The content analysis phase is where artificial intelligence really shines. The filter scans message bodies for suspicious keywords, unusual formatting, and social engineering tactics. It’s looking for the subtle signs that separate legitimate business emails from sophisticated phishing attempts.
URL filtering protects against malicious links by checking every embedded URL against real-time threat feeds. Suspicious links are either blocked outright or rewritten to route through security services for additional analysis.
Attachment scanning uses both traditional signature-based detection and modern behavioral analysis. Files are often executed in secure sandboxes—isolated environments where they can’t cause damage—to observe their actual behavior rather than just their appearance.
Bayesian analysis applies machine learning models trained specifically on your organization’s email patterns. This personalized approach helps identify subtle anomalies that generic rule-based systems might miss.
For more detailed information about spam detection specifically, check out our guide on Email Spam Filters: Boost Security.
Outbound Email Filtering
While everyone focuses on protecting against incoming threats, outbound email filtering quietly protects your organization’s reputation and prevents data breaches. It’s like having a security guard check what’s leaving the building, not just what’s coming in.
Data leak prevention scans every outgoing message for sensitive information patterns. The system recognizes credit card numbers, social security numbers, proprietary documents, and any content matching your confidentiality policies. One accidentally forwarded spreadsheet could expose customer data—outbound filtering catches these mistakes before they become headlines.
Compromised account detection monitors for unusual sending patterns that might indicate an employee’s email has been hacked. When someone suddenly starts sending hundreds of messages to random recipients, the filter knows something’s wrong and can stop the damage immediately.
Content policy enforcement ensures your outbound communications meet professional standards and regulatory requirements. This is especially important in industries like healthcare or finance where improper communications can result in hefty fines.
Transparent proxy systems can intercept outbound mail at the network level, applying security policies before messages ever leave your infrastructure. This approach catches everything, even emails sent from personal devices connected to your network.
5xx rejections allow your mail server to refuse delivery of policy-violating messages with appropriate error codes, giving users clear feedback about why their message was blocked.
This protection is crucial because once your organization’s IP addresses get blacklisted for sending spam, it can take weeks to restore your email reputation. During that time, even your legitimate business emails might end up in spam folders. For insights into how widespread this challenge has become, see this discussion on How Pervasive is ISP Outbound Email Filtering?.
Types & Techniques of Email Filters
Email filtering employs various techniques, each with strengths suited to different types of threats. Understanding these approaches helps you choose the right combination for your organization.
Content Filters examine the actual text and formatting of emails, looking for suspicious patterns, excessive capitalization, or known spam phrases.
Header Filters analyze the technical routing information that accompanies every email, checking for signs of spoofing or suspicious origins.
Blocklists maintain databases of known malicious IP addresses, domains, and email addresses that should never reach your inbox.
Safelists (also called allowlists) ensure that trusted senders always get through, even if their messages might otherwise trigger spam filters.
Bayesian Filters use statistical analysis to learn what constitutes normal email for your organization, becoming more accurate over time.
Heuristic Analysis applies rule-based logic to identify suspicious characteristics that might not appear in any single database.
AI and Machine Learning systems can detect subtle patterns and anomalies that traditional rule-based systems miss.
Greylisting temporarily rejects emails from unknown senders, relying on the fact that legitimate mail servers will retry delivery while spam systems typically won’t.
Reputation Scoring assigns trust levels to senders based on their historical behavior and third-party assessments.
Antivirus Integration scans all attachments for known malware signatures and behavioral indicators.
Sandboxing executes suspicious files in isolated environments to observe their behavior before allowing delivery.
Rule-Based & Heuristic Filters
Rule-based filters are the foundation of email filtering. They’re straightforward: if an email matches specific criteria, take a specific action. These filters excel at catching obvious spam and enforcing organizational policies.
Keyword Matching looks for specific words or phrases commonly found in spam. However, sophisticated spammers have learned to evade simple keyword filters by using character substitution or image-based text.
Regular Expression (Regex) Filtering provides more sophisticated pattern matching. For example, a regex can identify credit card numbers regardless of how they’re formatted or spaced.
RFC Violation Detection catches emails that don’t follow proper technical standards, which often indicates automated spam generation.
Sender Anomaly Detection flags emails from senders who deviate from normal patterns, such as suddenly sending high volumes or targeting unusual recipients.
The beauty of rule-based systems is their predictability and ease of management. When a rule triggers, you know exactly why. However, they require constant maintenance as spammers adapt their tactics.
Bayesian & Statistical Filters
Bayesian filters represent a major leap forward in email filtering sophistication. Instead of relying on predetermined rules, they learn from actual email patterns.
Probabilistic Scoring analyzes the frequency of words and phrases in both spam and legitimate emails, building statistical models that can identify subtle indicators humans might miss.
Self-Learning Capability means these filters improve over time. Every email you mark as spam or legitimate email helps refine the model.
Per-User Training allows the system to learn individual preferences. What one person considers spam (promotional emails) might be valuable to another (marketing professionals).
Accuracy Gains from Bayesian systems can be dramatic. While rule-based systems might achieve 85-90% accuracy, well-trained Bayesian filters often exceed 95%.
The key insight is that spam and legitimate email use language differently. Spam tends to use certain words more frequently, employ different grammar patterns, and follow predictable formatting conventions. Bayesian analysis can detect these patterns even when individual messages don’t trigger any specific rules.
AI-Driven & Machine-Learning Filters

Modern email filtering increasingly relies on artificial intelligence to combat sophisticated threats. These systems go far beyond traditional rule-based approaches.
Behavior Baseline Analysis establishes normal communication patterns for each user and department. When someone suddenly starts receiving emails from unusual sources or sending messages with different tone and content, the system flags these anomalies.
Anomaly Detection can identify zero-day phishing attempts that don’t match any known signatures. By analyzing subtle characteristics like writing style, link patterns, and sender behavior, AI can spot threats that humans and traditional filters miss.
Generative AI Threat Detection is becoming crucial as attackers use AI to create more convincing phishing emails. These messages can pass traditional filters because they’re grammatically correct and contextually appropriate.
Deep Learning Models can analyze images within emails to detect malicious content hidden in graphics, a technique that bypasses text-based filters entirely.
For the latest research on machine learning applications in spam detection, explore Scientific research on machine-learning spam detection.
Specialized Filters (Graymail, Language, Role-Based)
Beyond basic spam filtering, modern systems handle nuanced email management challenges.
Graymail Filtering addresses the growing problem of emails you technically subscribed to but don’t want. These might be newsletters you never read, promotional emails from old purchases, or notifications from services you rarely use. Advanced filters can identify these based on your interaction patterns.
Language Filters automatically route or block emails in languages your organization doesn’t use. This is particularly effective against international spam campaigns.
Role-Based Protection applies different filtering rules based on job function. Executives might receive stricter phishing protection, while marketing teams might need looser restrictions on promotional content.
VIP Policies ensure that emails from critical business partners, customers, or regulatory bodies never get caught in spam filters, even if they contain characteristics that might otherwise trigger alerts.
Benefits, Challenges & Best Practices
When you implement smart email filtering, you’re making an investment that pays dividends across your entire organization. The benefits are real and measurable, though like any technology solution, it comes with challenges that smart planning can overcome.
Risk reduction stands as the most compelling benefit. A well-configured filtering system blocks up to 99% of spam and catches most phishing attempts before they ever reach your team’s inboxes. This isn’t just about convenience—it’s about protecting your business from the kind of cyberattacks that can cost thousands in recovery time and lost productivity.
The productivity gains might surprise you. When your employees aren’t spending 15-30 minutes each day sorting through spam to find legitimate emails, that time goes back into meaningful work. Multiply that across your entire team, and you’re looking at hours of recovered productivity every single day.
Compliance support becomes effortless when your filtering system automatically archives communications and monitors content according to industry regulations. Whether you’re in healthcare, finance, or any other regulated industry, proper email filtering helps you meet those requirements without additional manual oversight.
Your IT security team will appreciate how effective filtering reduces SOC workload. When routine threats get handled automatically, your security professionals can focus their expertise on the sophisticated attacks that truly require human analysis.
But let’s be honest about the challenges. False positives remain every administrator’s biggest headache. When an important client email gets caught in the spam filter, it can damage relationships and create awkward explanations. The key is having systems in place to quickly identify and resolve these issues.
Filter evasion is an ongoing cat-and-mouse game. Cybercriminals constantly develop new techniques—hiding text in images, using character substitution, or creating messages that look completely legitimate. This is why your filtering solution needs regular updates and intelligent learning capabilities.
Performance impact can slow down email delivery if your system isn’t properly configured. However, modern cloud-based solutions typically handle this better than older on-premises systems, thanks to their distributed infrastructure and dedicated resources.
Privacy concerns deserve consideration, especially when content filtering examines personal communications mixed with business email. Clear policies and transparent communication with your team help address these concerns upfront.
Key Security Benefits
The security advantages of robust email filtering go far beyond keeping your inbox tidy. Think of it as your organization’s digital immune system, protecting against threats that could seriously damage your business.
Phishing protection tops the list of critical benefits. Modern phishing attacks are scary good at impersonating trusted brands, colleagues, even your CEO. These aren’t the obvious “Nigerian prince” scams anymore—they’re sophisticated attempts that can fool even tech-savvy employees. Advanced filters catch these by analyzing sender authentication, examining content patterns, and detecting behavioral anomalies that human eyes might miss.
Malware prevention stops viruses, ransomware, and other nasty software before they reach your computers. This includes both known threats that match existing signatures and unknown threats detected through behavioral analysis and sandboxing. When you consider that ransomware attacks can shut down entire businesses for days or weeks, this protection is invaluable.
Data loss prevention monitors your outbound communications to prevent accidental or intentional data breaches. Whether it’s a customer list accidentally attached to the wrong email or sensitive financial information being sent to unauthorized recipients, your filtering system acts as a safety net.
Brand protection ensures your email infrastructure can’t be hijacked to send spam. Once your organization’s IP addresses get blacklisted for sending unwanted emails, it can take weeks to restore your reputation and email deliverability.
For comprehensive strategies on protecting your inbox, check out our detailed guide on Email Spam Protection: Tips to Secure Inbox.
Common Limitations & How to Mitigate
Even the best email filtering systems have limitations, but knowing about them helps you plan effective workarounds.
False positive management requires clear procedures that your team can actually use. Your employees need an easy way to report legitimate emails caught in spam filters—ideally a simple button or forwarding address. More importantly, you need processes to quickly review these reports and adjust filtering rules so the same problem doesn’t happen repeatedly.
Encrypted payload challenges occur when malicious content hides within password-protected or encrypted attachments. Your filtering system can’t scan what it can’t see. The solution involves creating policies that require business justification for encrypted attachments and training your team on safe handling procedures.
Performance overhead doesn’t have to slow down your email if you plan properly. Cloud-based filtering services often provide better performance than on-premises solutions because they have distributed infrastructure specifically designed for email processing. If you’re experiencing slowdowns, it might be time to evaluate your current setup.
Integration complexity with existing email systems requires patience and careful testing. The smart approach involves pilot deployments with a small group of users, thorough testing of all email scenarios, and gradual rollouts that let you identify and fix compatibility issues before they affect everyone.
Best Practices for Effective Email Filtering
Success with email filtering comes from following proven best practices that organizations have refined over years of experience.
Multi-layer defense means not putting all your eggs in one basket. Instead of relying solely on content filtering or reputation checking, the most effective approaches combine different techniques. Think reputation filtering working alongside content analysis, backed up by sandboxing for suspicious attachments, all supported by user education. When one layer misses something, the others catch it.
DMARC, SPF, and DKIM implementation provides strong sender authentication that makes spoofing much harder. These protocols work together like a three-factor authentication system for email, verifying that messages actually come from their claimed sources and haven’t been tampered with during delivery.
Regular rule review and updates keep your filtering effective as threats evolve. This means actually looking at quarantined emails periodically, adjusting score thresholds based on false positive reports, and updating your allowlists and blocklists as business relationships change.
Threat intelligence integration keeps your filters current with the latest attack patterns identified by security researchers worldwide. The best filtering systems automatically receive these updates, but you should verify that your solution includes this capability.
User reporting mechanisms create feedback loops that make your system smarter over time. When employees can easily report false positives and false negatives, your filtering system learns and adapts to your organization’s unique communication patterns.
Phishing simulation programs test both your technical controls and user awareness simultaneously. Regular simulated attacks help you identify gaps in filtering effectiveness while keeping security awareness fresh in your team’s minds.
Continuous monitoring and tuning involves regularly reviewing performance metrics, adjusting policies as your business needs change, and staying informed about emerging threats. This isn’t a “set it and forget it” technology—it requires ongoing attention to remain effective.
Choosing & Customizing Your Email Filtering Solution
Picking the right email filtering solution can feel overwhelming with so many options available. But don’t worry—we’ll walk you through the key decisions that matter most for your business.
The first big choice is between cloud-based Secure Email Gateways and on-premises appliances. Cloud solutions handle all the heavy lifting for you—automatic updates, scaling during traffic spikes, and no server maintenance headaches. On-premises appliances give you complete control over your data and settings, but they also mean your IT team becomes responsible for updates, maintenance, and capacity planning.
Most businesses today lean toward cloud solutions because they’re simply easier to manage. Your team can focus on running your business instead of babysitting email servers.
The free versus enterprise debate comes down to what level of protection and support your organization needs. Free solutions work fine for basic spam blocking, but they’re like having a simple door lock when you might need a full security system. Enterprise solutions bring advanced threat detection, detailed reporting, and—crucially—someone to call when things go wrong.
Open-source options like SpamAssassin offer incredible flexibility if you have the technical expertise to configure and maintain them. Commercial solutions provide polished interfaces and professional support, which can be worth every penny when you’re dealing with a critical email issue at 2 AM.
Modern AI capabilities are becoming essential rather than nice-to-have features. The best systems learn your organization’s email patterns and can spot threats that traditional rule-based filters miss entirely.
Free vs Enterprise Email Filtering – Which Fits You?
| Feature | Free Solutions | Enterprise Solutions |
|---|---|---|
| Spam Detection | Basic keyword/reputation | Advanced AI/ML analysis |
| Phishing Protection | Limited | Comprehensive behavioral analysis |
| Customization | Minimal | Extensive policy controls |
| Reporting | Basic logs | Detailed analytics and dashboards |
| Support | Community forums | 24/7 professional support |
| Scalability | Limited users | Enterprise-scale deployment |
| Integration | Basic SMTP | Full API and platform integration |
| Compliance | Self-managed | Built-in compliance tools |
| Cost | Free | Subscription-based |
If you’re a small business with basic needs and someone tech-savvy on your team, free solutions might work perfectly. They’re ideal for startups that need protection but are watching every dollar.
Enterprise solutions become essential when you’re handling sensitive customer data, need to meet regulatory requirements, or simply don’t have the internal expertise to manage security systems. The subscription cost pays for itself through reduced risk and the peace of mind that comes with professional support.
Custom Rules & Policy Tuning
Here’s where email filtering gets interesting—making the system work exactly how your business needs it to work.
Custom rules let you create specific protections for your unique situation. For example, you might set up patterns to catch credit card numbers in outbound emails (\b\d{4}[\s-]?\d{4}[\s-]?\d{4}[\s-]?\d{4}\b) or flag emails mentioning executives and financial terms together ((CEO|President|CFO|urgent|wire transfer)).
Role-based policies recognize that different people in your organization face different email threats. Your executives need extra protection against targeted phishing attacks. Your marketing team needs looser restrictions because they legitimately receive promotional content. Customer service needs to receive complaints and feedback that might otherwise look like spam.
Quarantine workflows should be simple for your users. When an email gets held for review, people need to know about it quickly and have an easy way to release legitimate messages. Nobody should need a computer science degree to get their emails back.
Safe and block list maintenance requires regular attention. Business relationships change, new partners join your network, and old threats become irrelevant. Set aside time monthly to review these lists and keep them current.
For deeper insights into filtering fundamentals, check out our guide on What is Email Filtering?. When you’re ready to evaluate specific solutions, our Email Spam Filter Checkers Guide provides practical testing approaches.
Integration & Deployment Checklist
Rolling out email filtering successfully requires careful planning, but it doesn’t have to be stressful.
Platform compatibility comes first. Whether you’re using Microsoft 365, Google Workspace, or another email system, make sure your chosen filtering solution integrates smoothly. The last thing you want is to find compatibility issues after you’ve already committed to a solution.
SIEM and DLP integration matters if you have other security tools in place. Your filtering system should feed information into your broader security monitoring, creating a complete picture of threats targeting your organization.
Performance testing prevents nasty surprises. Test how the system handles your typical email volume, measure any delays it introduces, and make sure it won’t become a bottleneck during busy periods.
Pilot deployment with a small group lets you work out the kinks before affecting everyone. Choose a mix of technical and non-technical users who can provide good feedback about both functionality and user experience.
Rollback planning gives you an escape route if something goes wrong. Know exactly how to restore your previous email setup quickly if needed.
User communication sets expectations and reduces support calls. Let people know what’s changing, when it’s happening, and who to contact with questions.
For additional deployment insights, Inbound and Outbound Email Filtering offers practical perspectives from other organizations.
The key is taking it step by step. Good planning up front saves hours of troubleshooting later.
Frequently Asked Questions about Email Filtering
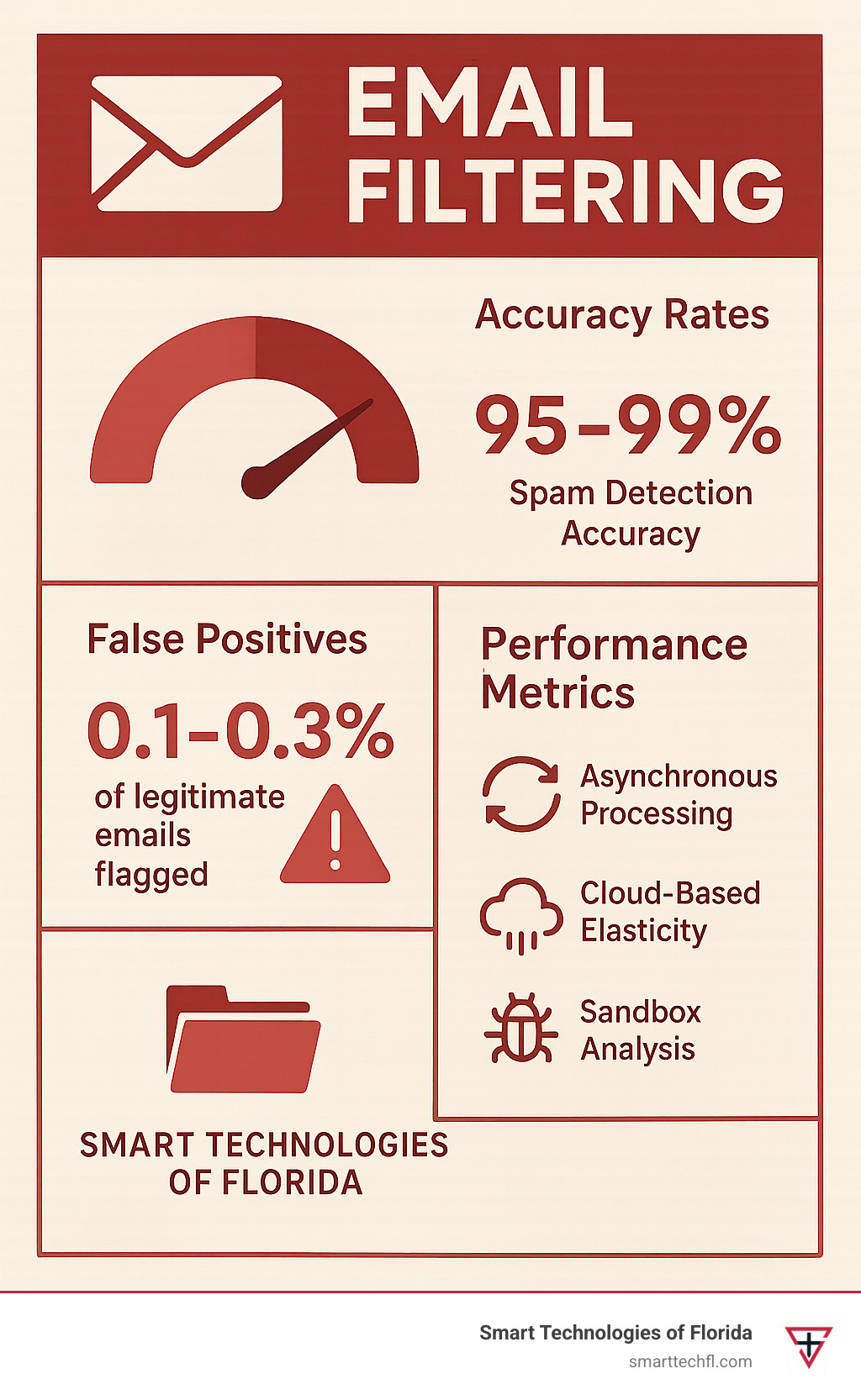
How accurate is modern email filtering and what about false positives?
You’re probably wondering if email filtering actually works or if you’ll end up missing important emails. The good news? Modern systems are remarkably accurate.
Today’s email filtering combines Bayesian statistics with AI analysis to achieve 95-99% accuracy for spam detection. That’s a huge improvement from the 80-85% rates we saw just a few years ago.
But let’s be honest about false positives—they still happen. The trick is setting up your system to minimize them. Safelist configuration is your best friend here. Add your key business partners, vendors, and customers to your trusted sender list so their emails always get through.
User feedback mechanisms make all the difference. When your team can easily click “this isn’t spam” on quarantined emails, the system learns fast. Think of it like training a smart assistant who gets better at understanding your preferences over time.
The smartest systems don’t make simple yes-or-no decisions. Instead, they use confidence scoring. Obvious spam gets blocked immediately. Borderline cases go to quarantine where humans can review them. This approach dramatically cuts false positives while keeping your inbox clean.
Does email filtering slow down mail delivery?
This is probably your IT team’s biggest concern, and it’s a fair one. Nobody wants emails crawling to a halt because of security measures.
Here’s the reality: well-designed email filtering adds only microseconds to seconds to delivery time. Most people never notice the difference.
Modern systems use asynchronous processing, which is a fancy way of saying they multitask really well. While one part scans for malware, another checks sender reputation simultaneously. It’s like having multiple security guards working in parallel instead of making you wait in multiple single-file lines.
Cloud-based filtering services have virtually unlimited processing power. Unlike that server sitting in your closet that gets overwhelmed during busy periods, cloud systems scale up automatically when email volume spikes.
Sandbox analysis happens behind the scenes. Clean emails zip through to your inbox immediately. Only suspicious attachments get the full treatment in isolated testing environments, and that doesn’t slow down your regular mail flow.
How do I train filters to recognize my unique mail flow?
Every organization has its own email personality. Your marketing team gets different mail than your accounting department. Your industry has specific communication patterns. Smart email filtering learns these nuances.
User feedback is absolutely crucial. Make it dead simple for your team to mark emails as spam or legitimate. Most systems have one-click options right in the quarantine notifications. The more feedback you provide, the smarter the system becomes about your specific needs.
Adaptive learning models work continuously in the background. They figure out which senders you trust, what types of content are normal for your business, and how your team typically communicates. It’s like having a personal assistant who learns your preferences without you having to explain everything.
Set up periodic review sessions to examine quarantined emails. You’ll quickly spot patterns—maybe the system is being too aggressive with newsletter-style emails, or perhaps it needs tighter rules around financial communications.
Custom training data can jumpstart the process. By analyzing your organization’s email history, the system builds baseline models before you even go live. This means better accuracy from day one instead of weeks of learning.
The key is patience and consistency. Like any learning system, email filtering gets better with time and attention. Most organizations see significant improvement in accuracy within the first month of active training.
Conclusion
Think of email filtering as your business’s digital immune system. Just like your body fights off infections before you even notice them, effective filtering stops threats before they reach your team’s inboxes. And honestly? With cybercriminals getting craftier every day, this protection isn’t just nice to have—it’s absolutely essential.
Here’s the reality: 45% of all emails are spam, and the bad guys aren’t just sending obvious “get rich quick” schemes anymore. They’re using AI to craft convincing phishing emails that can fool even tech-savvy employees. Your business needs filtering that’s just as smart as the threats it’s facing.
At Smart Technologies of Florida, we’ve spent 23 years helping businesses steer digital challenges, and we’ve learned something important: the best technology solutions are the ones that actually work for real people. That’s why our approach to email filtering goes beyond just installing software. We design systems that understand how your team actually communicates and work seamlessly with your existing processes.
The secret sauce isn’t just having good filters—it’s having the right combination of AI-driven analysis, user-friendly policies, and ongoing fine-tuning that adapts to your business. Think of it like training a really smart security guard who learns your company’s patterns and gets better at spotting trouble over time.
What we love about modern filtering systems is how they’ve evolved beyond simple spam blocking. Today’s solutions can detect sophisticated phishing attempts, prevent data breaches through outbound monitoring, and organize emails intelligently while staying virtually invisible to your users. When done right, people barely notice the filtering is there—they just notice that their inboxes are cleaner and more secure.
But here’s what many businesses miss: email filtering isn’t a “set it and forget it” solution. It needs regular attention, just like any other important business system. The filters that work best are the ones that get regular updates, user feedback, and adjustments based on your changing business needs.
The investment in comprehensive email security pays for itself quickly. When your team isn’t wasting time sorting through spam or recovering from phishing attacks, they can focus on what actually grows your business. Plus, you’ll sleep better knowing your organization’s sensitive information is protected.
Ready to give your business the email protection it deserves? We specialize in creating email filtering strategies that actually make sense for your organization. No cookie-cutter solutions—just thoughtful, people-centered security that works the way you do business.
Learn more about how we can transform your business security through our Managed IT Solutions.












